A Biased View of Google Authority Stack Service
Some Known Details About Google Authority Stack Service
Table of ContentsThe Buzz on Google Authority Stack ServiceSome Ideas on Google Authority Stack Service You Should KnowNot known Incorrect Statements About Google Authority Stack Service Everything about Google Authority Stack ServiceThe Best Guide To Google Authority Stack ServiceSome Of Google Authority Stack Service
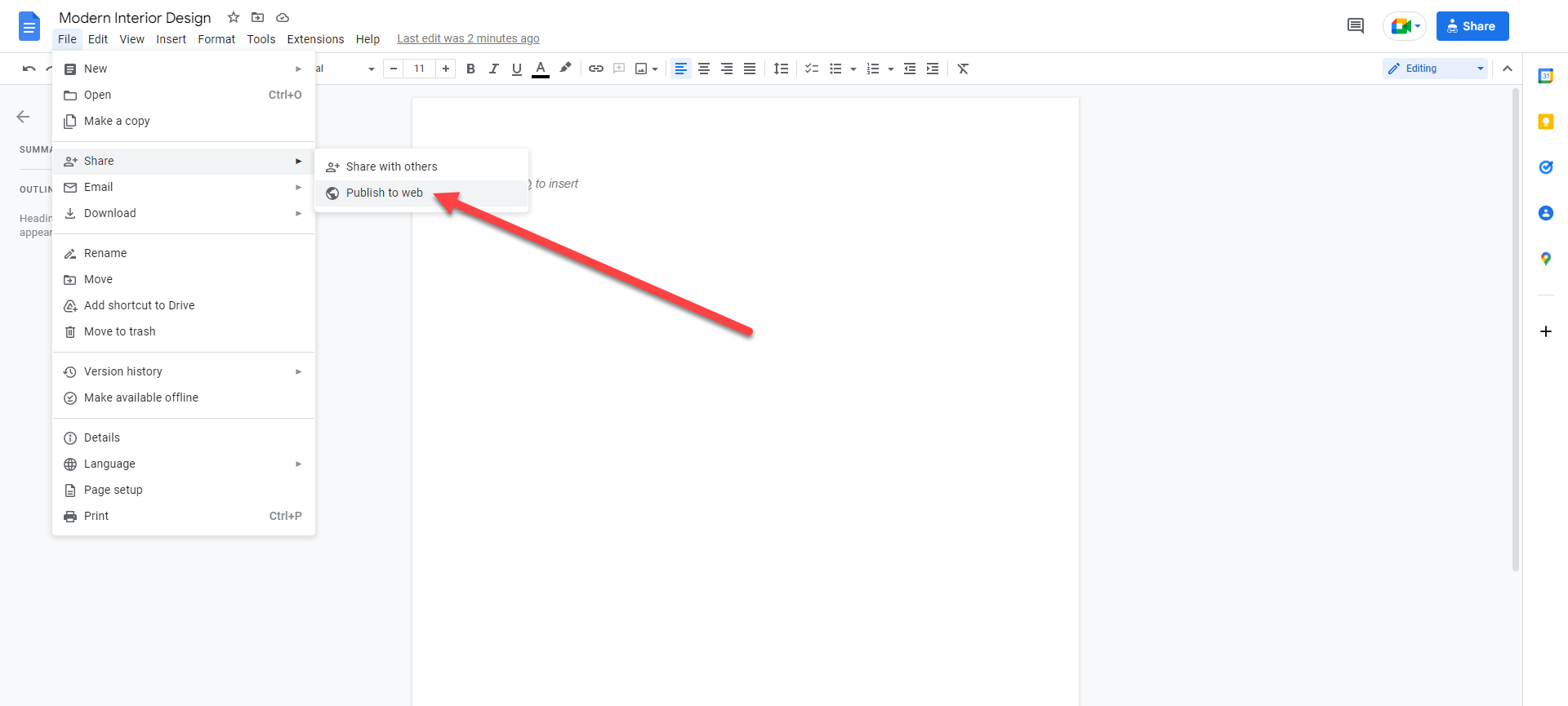
Follow the below screenshot to recognize it much better - Google Authority Stack Service. Search your address on the google my map search area After that add the Title as well as Summary of the map layer and also customized the map symbol as well as upload pictures from google drive or images. After that copy the real-time link and paste it right into the sheet.Like prior to replicating the public link and also paste it into a google sheet For this reason, Google stack can be made just from google entities than the very best source of the video is You, Tube, So share your motion graphics on youtube and on the summary area share your home web page link also share social links as well as duplicate the link and also paste it right into google sheet exact same as previously.
Gather all positive google evaluations as well as replicate the share link as well as paste it right into a google stand out sheet. After collecting all data from the google entity share the google sheet into anybody can watch it on the real-time web link. Gather all information of google other entities and embed the code into google websites by adding unique web content based upon emphasis search phrases.
The Basic Principles Of Google Authority Stack Service
We really did not locate any application that matches with your search.

Timeline templates are affixed to regulations and also utilize predefined questions when informs are explored. Timelines can be conserved as well as shown to others, along with affixed to Instances. Cases: An inner system for opening, monitoring, and also sharing security issues directly in the Safety app. Cases can be integrated with outside ticketing systems.
The Only Guide for Google Authority Stack Service
The Fleet application is used to mount and also manage Elastic Professionals and also combinations on your hosts. Self-protection implies that Elastic Endpoint has guards against individuals and enemies that might attempt to interfere with its functionality. This security function is constantly enhanced to avoid attackers that may try to use newer, a lot more advanced strategies to disrupt the Elastic Endpoint.
The complying with areas advise safety tools and modern technologies to develop a protected foundation for the web servers running anchor the Azure Stack HCI running system in your environment. This section goes over exactly how to protect services and also digital equipments (VMs) running on the operating system: supplies consistent Secure Boot, UEFI, and also TPM setups out of the box.
For more details, see Azure Update Administration utilizing Windows Admin Facility. This area discusses exactly how to utilize Windows Admin Facility to shield data and also workloads on the os: shields information at remainder. You can make use of Little bit, Storage locker to secure the components of Storage Spaces information volumes on the operating system.
Everything about Google Authority Stack Service
It likewise gives single sign-on (SSO) for Remote Desktop computer sessions. Throughout a Remote Desktop computer session, if the target gadget is compromised, your credentials are not revealed due to the fact that both credential and credential derivatives are never passed over the network to the target tool.
We make use of some necessary cookies to make this web site work. We want to establish additional cookies to recognize just how you make use of GOV.UK, remember your settings and enhance federal government solutions. We likewise use cookies established by other sites to aid us supply web content from their services.
The Ultimate Guide To Google Authority Stack Service
As well as the simplest method to do this is by contrasting how cloud indigenous applications differ to heritage systems. Pre-containers and also pre-cloud, applications were organized on physical servers that were kept within an organisation's own information centre. Once done, VMs would be treated in precisely the exact same means as a physical server would be.
Virtualization was the primary step in the direction of far better source exercise - as well as although organisations would still require see this site to run various operating systems like this (O/S) within a web server - you could begin to deploy various work on a single equipment. Now, the contemporary means to deploy new work is via containers. What Is Google Authority, And How Does It Relate To Google Stack. Containers share much of the exact same logic as virtualization because they're an abstraction of equipment - yet containers go one action further by abstracting the O/S as well.
All About Google Authority Stack Service
Basically, Kubernetes is a centralised administration platform that assists ensure that containers are going to their required spec. Aiding you scale your applications to restrain with need. We don't want this phase to become as well technological - yet one principle we do require to touch on is clusters.
The fact that it fixes an extremely genuine problem that programmers are encountered with on a practically constant range. We already recognize that cert-manager is released inside a Kubernetes collection for the objective of issuing and also restoring X. 509 maker identities - however in this area we take a closer consider how it functions.
Essentially, cert-manager secures cloud native work by releasing and renewing certificates that have been acquired as component of a PKI. In regards to circulation, Issuers are a Kubernetes source that represents a CA. This is the resource type that will produce the authorized certifications when a demand is made by cert-manager.